Analyze System Calls with Stratoshark: Wireshark for Cloud Systems

Diagnosing system-level issues in cloud and container environments requires visibility into syscalls, file I/O, and process interactions. Network packet analysis tools like Wireshark revolutionized troubleshooting, but no equivalent existed for system call traces—until now. Stratoshark extends Wireshark's proven interface and filtering engine to analyze system activity captured from Linux hosts and containers.
What is Stratoshark?
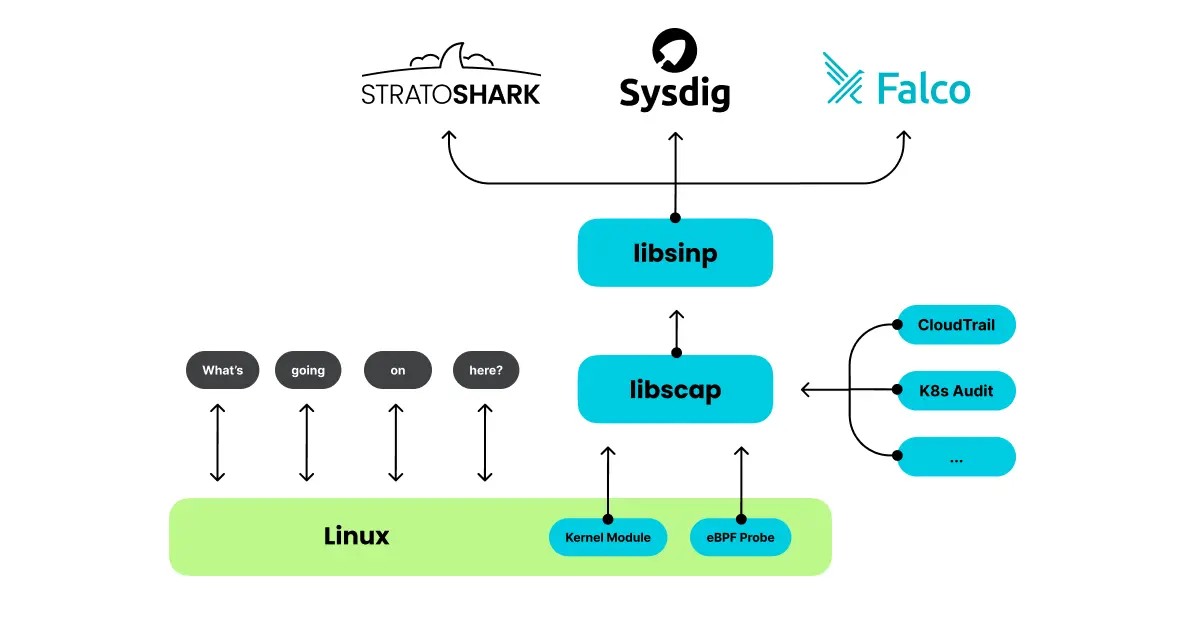
Stratoshark is a companion application to Wireshark designed for analyzing system calls and log messages. Created by Gerald Combs and Loris Degioanni—the original Wireshark developers—it applies the same three-pane interface and display filtering philosophy to system event data. Stratoshark uses libsinsp and libscap libraries to parse captures from Sysdig and Falco, enabling operators to investigate performance bottlenecks, security incidents, and application behavior at the syscall level.
Key Features
- Wireshark-Style Interface: Navigate system events with familiar packet list, detail, and byte panes for rapid analysis.
- Sysdig Integration: Opens
.scapfiles generated by Sysdig to examine file opens, network connects, process executions, and IPC activity. - Advanced Filtering: Leverage Wireshark's display filters to isolate specific processes, syscall types, or file descriptors.
- Falco Plugin Support: Includes the Falco CloudTrail plugin on Windows and macOS for analyzing cloud provider audit logs.
- Container Awareness: Correlates syscalls with container metadata for troubleshooting Kubernetes and Docker workloads.
Installation
Download platform-specific packages from stratoshark.org:
Windows and macOS: Install the prebuilt package directly.
Linux: Build from source using the Wireshark codebase. First, install dependencies:
sudo apt install -y cmake g++ libglib2.0-dev libpcap-dev \
qtbase5-dev qttools5-dev-tools libsystemd-dev
Clone the Wireshark repository and build with Stratoshark enabled:
git clone https://gitlab.com/wireshark/wireshark.git
cd wireshark
cmake -DBUILD_stratoshark=ON .
make -j$(nproc)
sudo make install
Install Sysdig to generate capture files:
curl -s https://s3.amazonaws.com/download.draios.com/stable/install-sysdig | sudo bash
Usage
Capture system activity with Sysdig, then analyze it in Stratoshark:
# Capture all system calls for 60 seconds
sysdig -w capture.scap
# Capture only nginx process activity
sysdig -w nginx.scap proc.name=nginx
# Capture file open syscalls with extended payload
sysdig -s 1000 -w fileops.scap evt.type=open
Open the .scap file in Stratoshark and apply display filters to isolate events. For example, filter to show only write syscalls from a specific PID:
evt.type == "write" and proc.pid == 1234
Stratoshark displays event timestamps, call direction (entry/exit), process details, and file descriptor information—all navigable through the familiar Wireshark UI.
Operational Tips
- Combine with Falco: Capture syscalls during a Falco alert to correlate security events with underlying system activity.
- Reference Man Pages: Use Linux syscall documentation (
man 2 <syscall>) to interpret event parameters and return values. - Filter Early: Apply Sysdig capture filters to reduce file size and focus on relevant processes or syscall types before opening in Stratoshark.
- Trace Container Issues: When debugging container networking or file access problems, capture at the host level to see syscalls from all containers simultaneously.
Conclusion
Stratoshark brings Wireshark's power to system call analysis, enabling SREs to troubleshoot complex Linux and container issues with a proven interface. Its integration with Sysdig and Falco makes it indispensable for performance tuning and security investigations.
For efficient incident management and to prevent on-call burnout, consider using Akmatori. Akmatori automates incident response, reduces downtime, and simplifies troubleshooting.
Additionally, for reliable virtual machines and bare metal servers worldwide, check out Gcore.
