How to Disable TLS 1.0 and TLS 1.1 in Nginx

Securing your web server is critical. One way to do this is by disabling outdated TLS protocols. This guide will show you how to disable TLS 1.0 and TLS 1.1 in Nginx.
Why Disable TLS 1.0 and TLS 1.1?
TLS 1.0 and TLS 1.1 are outdated. They have known security vulnerabilities. Disabling these protocols improves your server's security. It ensures your server uses more secure versions, like TLS 1.2 and TLS 1.3.
Prerequisites
Before we start, ensure you have:
- A running instance of Nginx
- Access to the Nginx configuration file
- Basic knowledge of editing configuration files
Step-by-Step Guide
1. Locate the Nginx Configuration File
The main configuration file is usually found at /etc/nginx/nginx.conf. For site-specific settings, check the configuration files in /etc/nginx/sites-available/ or /etc/nginx/conf.d/.
2. Backup the Configuration File
Always backup your configuration file before making changes. Use this command:
sudo cp /etc/nginx/nginx.conf /etc/nginx/nginx.conf.bak
3. Edit the Configuration File
Open the configuration file in your preferred text editor:
sudo nano /etc/nginx/nginx.conf
4. Update the ssl_protocols Directive
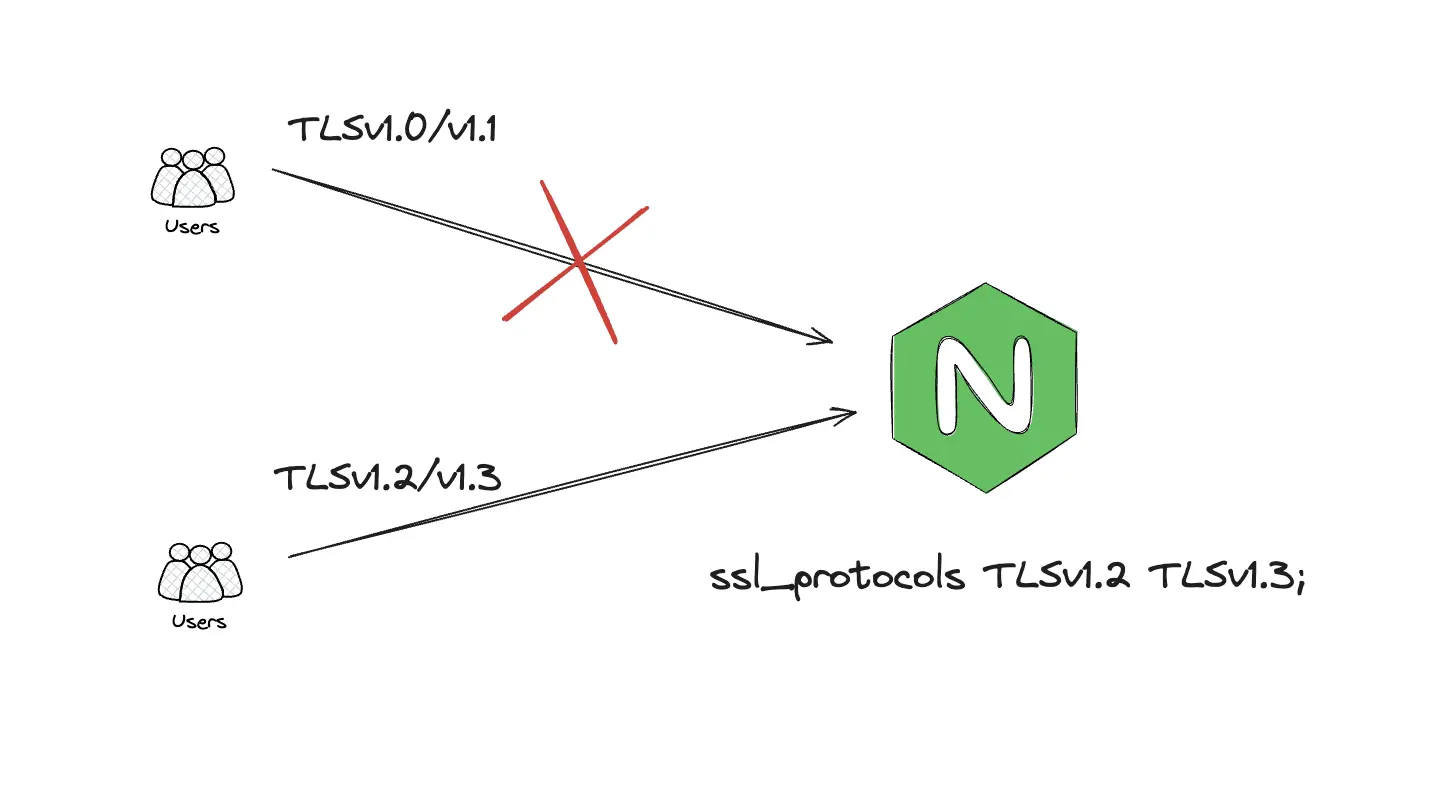
Find the ssl_protocols directive. It specifies which TLS versions Nginx will use. Modify it to only include TLS 1.2 and TLS 1.3:
ssl_protocols TLSv1.2 TLSv1.3;
5. Save and Exit
Save the changes and exit the text editor. In nano, you can do this by pressing CTRL + X, then Y, and Enter.
6. Test the Configuration
Before reloading Nginx, test the configuration for syntax errors:
sudo nginx -t
7. Reload Nginx
If the test is successful, reload Nginx to apply the changes:
sudo nginx -s reload
Verify the Changes
To ensure TLS 1.0 and TLS 1.1 are disabled, you can use online tools like SSL Labs' SSL Test or command-line tools like openssl.
Using SSL Labs
- Go to SSL Labs' SSL Test.
- Enter your domain and start the test.
- Review the results to ensure only TLS 1.2 and TLS 1.3 are enabled.
Using OpenSSL
Run the following command to check the supported protocols:
openssl s_client -connect yourdomain.com:443 -tls1
Replace yourdomain.com with your actual domain. If TLS 1.0 is disabled, the command should fail. Repeat this for -tls1_1 to check TLS 1.1.
Common Issues and Troubleshooting
Error: "ssl_protocols directive is duplicate"
This error occurs if the ssl_protocols directive is defined multiple times. Ensure it's only set once in your configuration.
Error: "Unsupported protocol"
Ensure your Nginx version supports TLS 1.3. You may need to upgrade Nginx if it's an older version.
Conclusion
Disabling TLS 1.0 and TLS 1.1 in Nginx enhances your server's security. This guide showed you how to make these changes safely. For even better performance and security, consider using Akmatori, a globally distributed TCP/UDP load balancer. Akmatori ensures your services stay secure, available, and performant.
